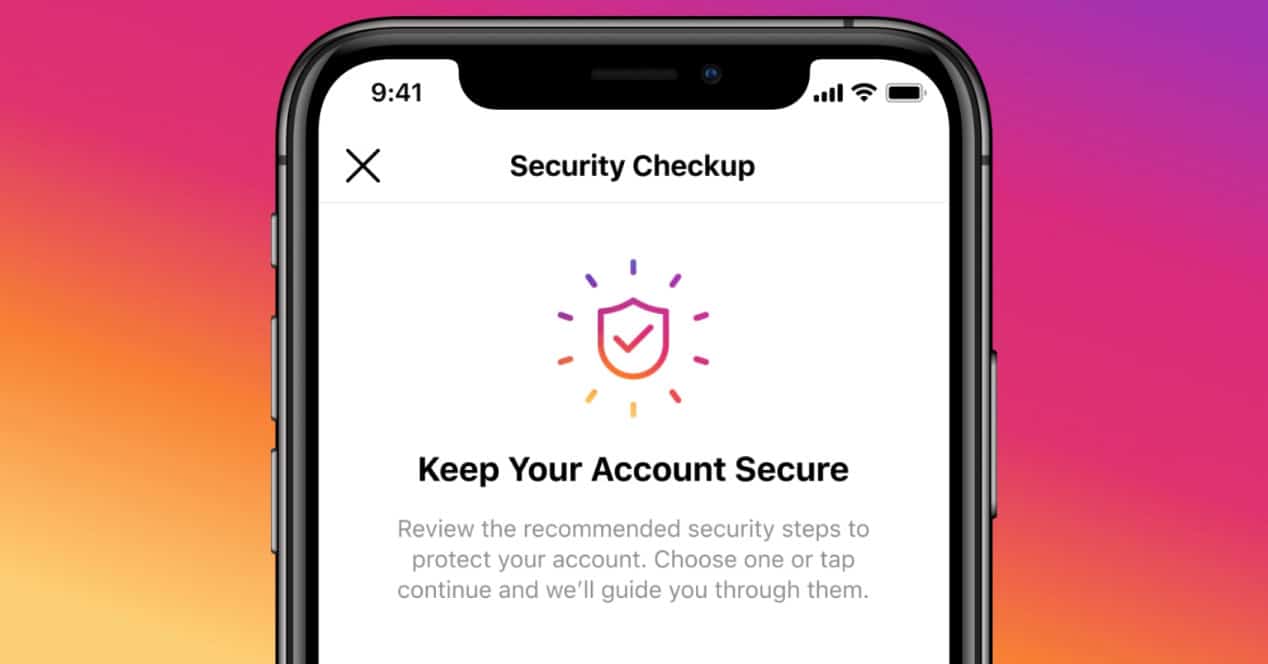
Security Checkup is the new tool that Facebook has announced for Instagram. This includes a series of functions that will prevent you from losing control of your account or even recover it if necessary. At least that's the idea. So we are going to tell you in detail what it consists of.
Do not lose control of your Instagram profile
One of the worst things that can happen to you or any other user of any current social network or platform is trying to access it and not being able to. For this reason, for several years now there has been a lot of emphasis on the use of strong passwords and other methods of protection against unauthorized access.
Among all these measures, the option of double safety factor It has been the most important of all. So much so that today it is difficult to find platforms that do not offer this option among their security options. Because by using a series of codes or verification methods in real time and valid only for a certain period, it is very complicated that, if they find out your password, you can lose control.
Well, to all those options that were already available on Instagram, now a new one is added, or rather, a new section or section that will help you verify that your account is protected in the best possible way. Also helping you to recover it if necessary.
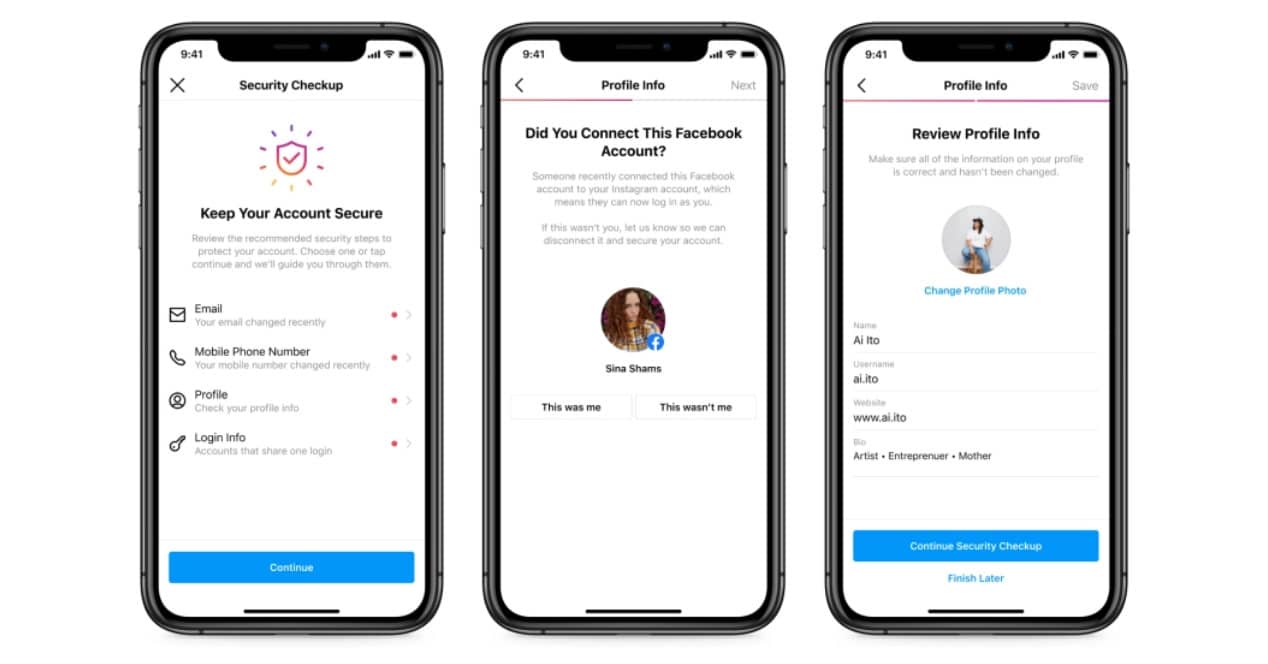
Security Checkup or security check is the name of a new section that if you don't already see it in your Instagram app, it won't take long for it to appear. In it you can find a series of sections to review with which you can make sure that everything is under control. These are the following:
- Associated email
- Mobile phone number
- Profile info
- Login information
In addition, you can also verify if when you connect a Facebook account, for example, it was you or not. You will even be able to review and update personal information so that in case you lose access you can recover it when they ask you for certain verification data to verify that it is you.
WhatsApp as a double verification system and more
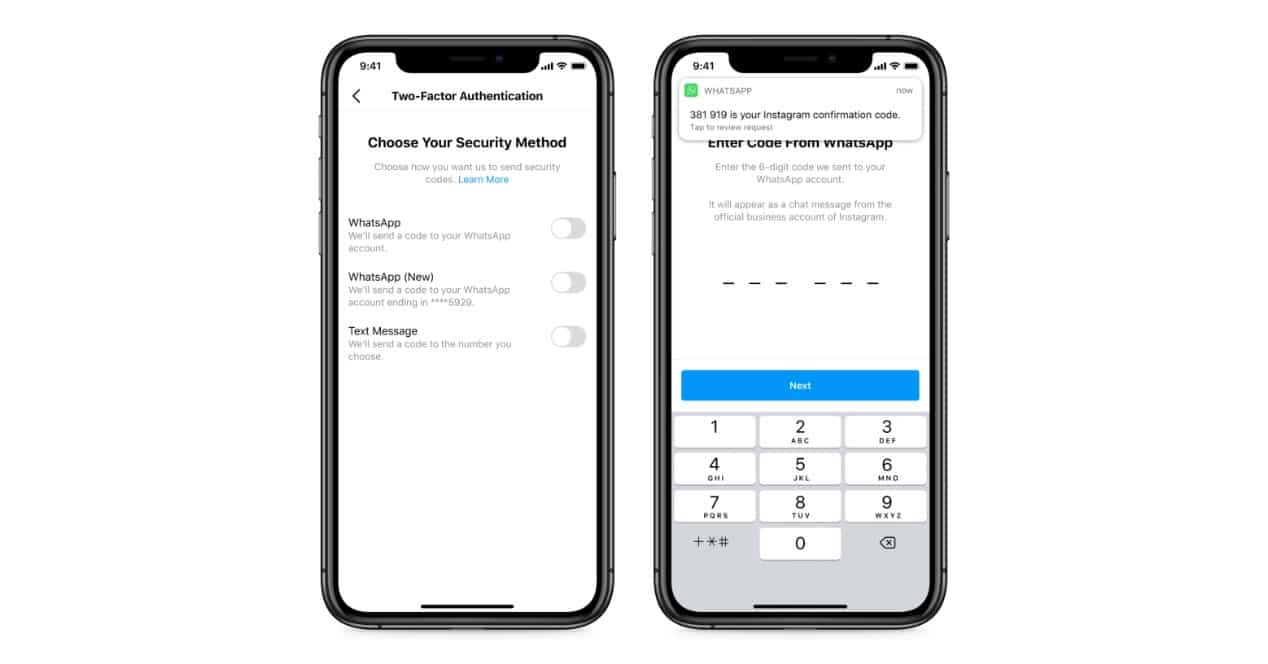
Along with this new Security Check section, Instagram also mentions how important it is to enable measures that already exist and reports a novelty that will soon arrive in a list of countries that have not yet confirmed: use WhatsApp as a two-step verification method.
That's somewhat similar to what you might see with Google accounts and using YouTube or the Google Home app as a login verification system. Facebook will use its messaging service to send there the messages with the numerical code necessary to verify that it is you who is trying to access your Instagram profile.
A solution that comes to replace the use of SMS text messages, a valid option also despite the problems that have existed in the past due to techniques such as SIM swapping. And that, by the way, is very easy to activate:
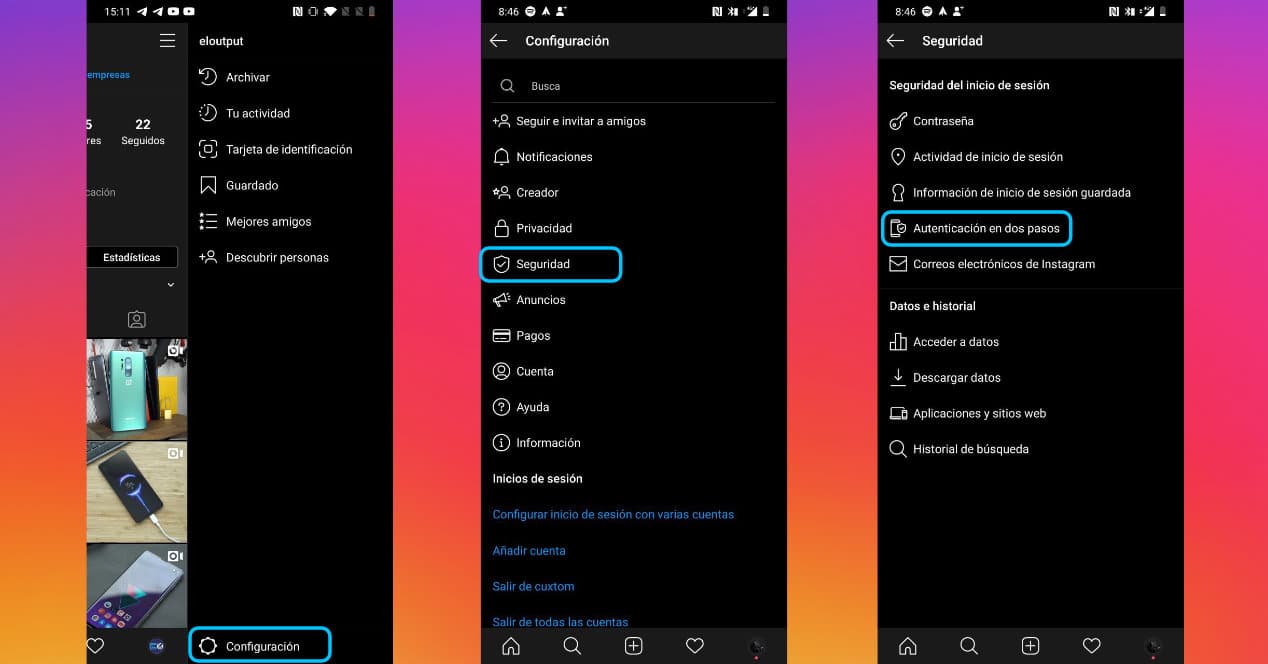
- Open the Instagram app on your Android or iOS phone
- Go to Settings setting of Instagram
- Select option Security
- Now choose Two-step authentication
- There you will see two options: text message and Authenticator application
- Choose the option that interests you the most (you can opt for both if you want) and follow the steps indicated.
Instagram protection measures
In summary, with these Instagram news, it could be said that the social network significantly improves its security measures. So there should be no problems with unwanted access or regaining control. But if you like, a summary with the recommendations that Facebook gives now that it has new tools.
- Use the two step verification: regardless of the method you prefer when receiving the code, from SMS to those future WhatsApp messages, this is a basic measure since everyone should have it active
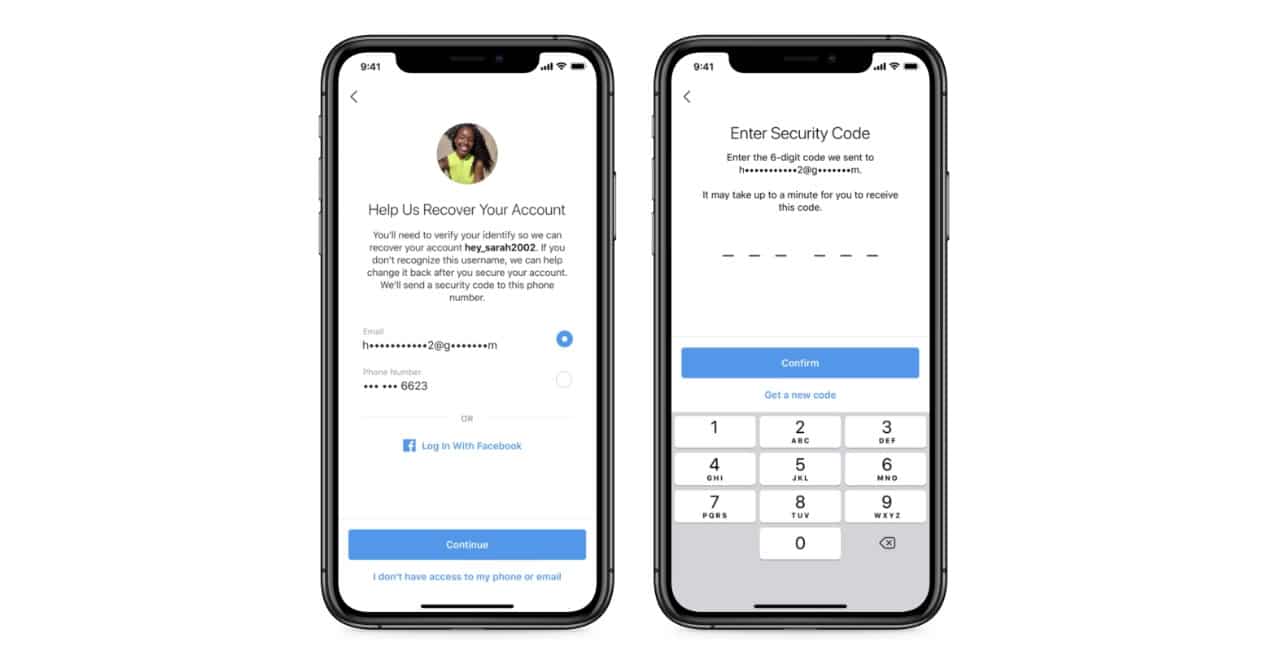
- Update email data and phone. This is important if you want to be able to recover your account if you lose control and even if the account accessor quickly changes your personal information associated with it.
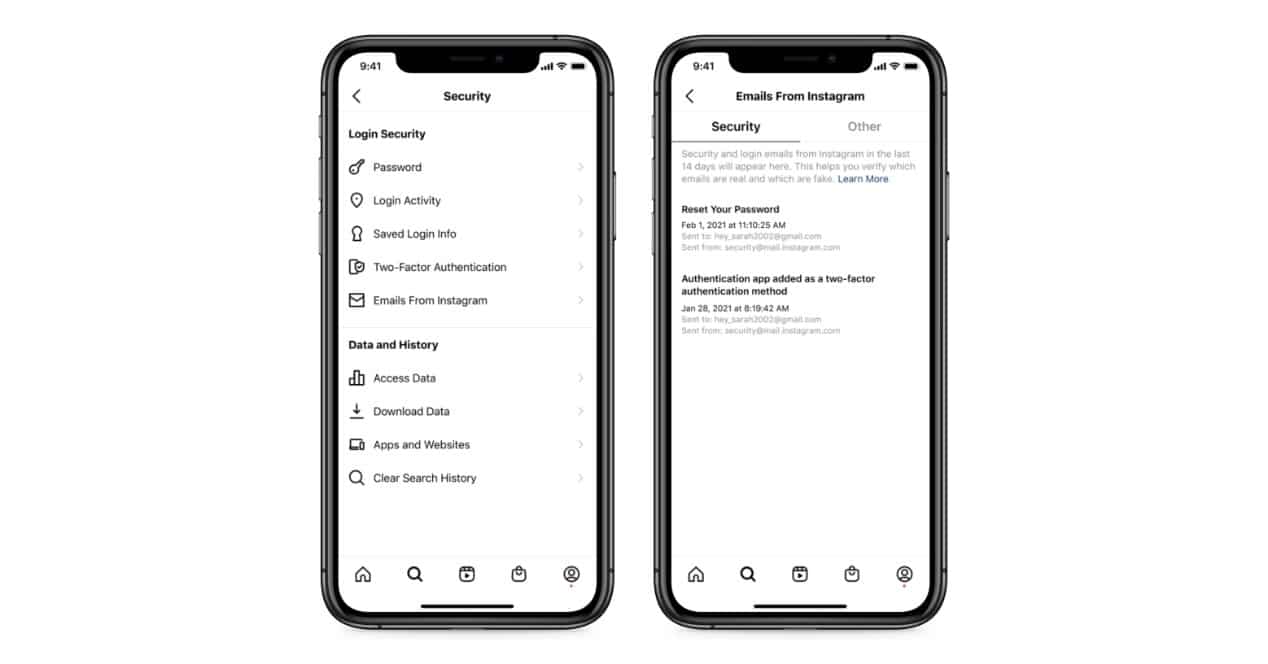
- Instagram will never contact via DM. This is something of an online security first, but still many users end up falling for it. Social networks and other online platforms will never contact via direct message to request possible security codes to access an account. So in case you receive a message asking you to provide said code (whether from the app that is) never give it
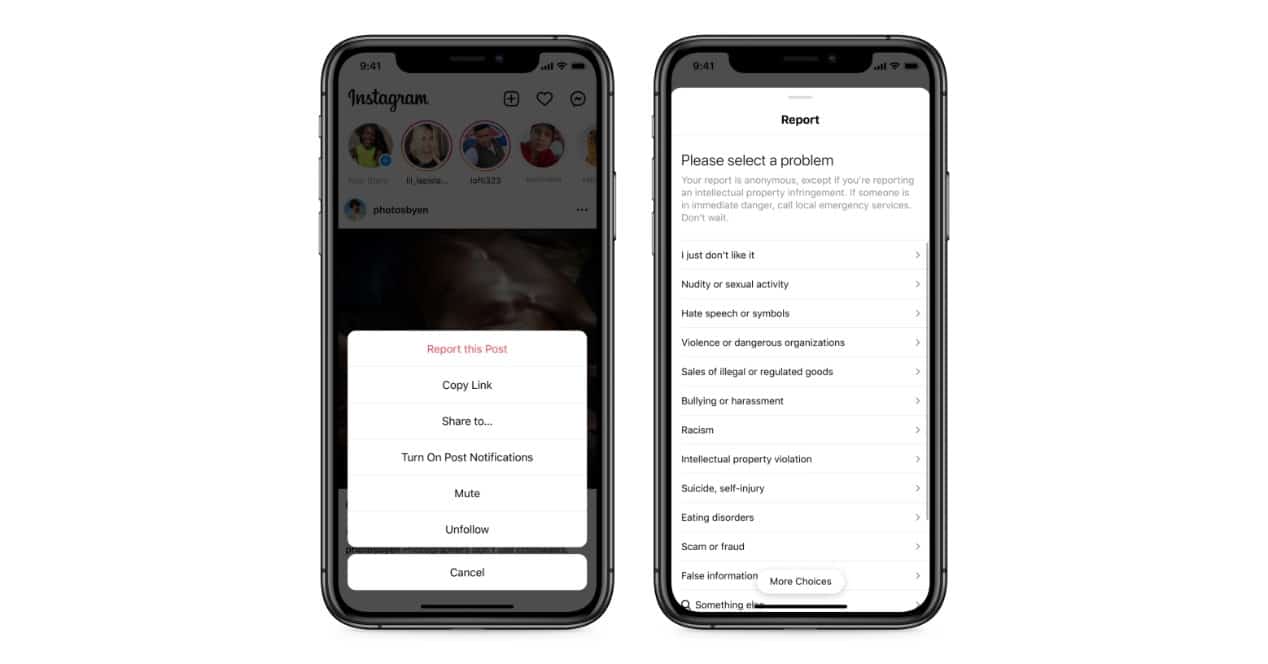
- Report questionable content and accounts. This measure is more focused on prevention, but if you receive any messages or see activity on profiles with a dubious reputation: report them so they can verify whether or not they are breaking the rules and putting the safety of other users at risk
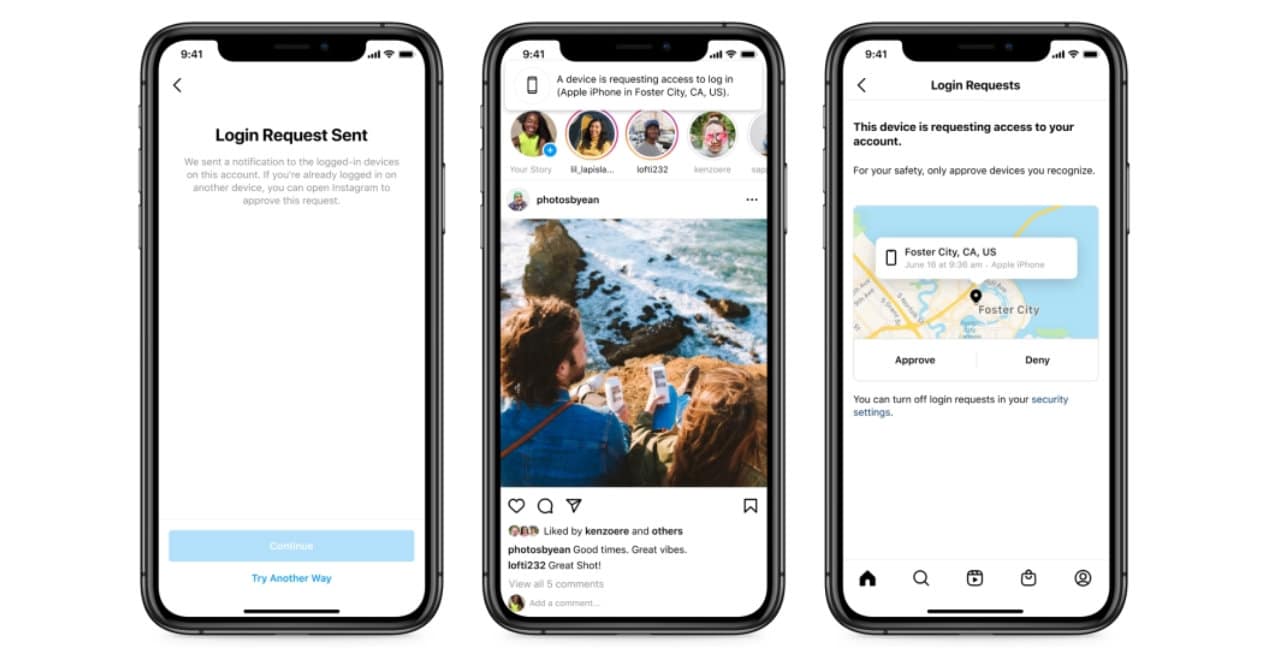
- Enable the login request. This option allows you to receive a notification telling you if and from where someone is trying to log into your account, regardless of whether it's a mobile device or browser. If Instagram does not know it, it will alert you and you will be the one to indicate whether you are aware of it and want to allow it to do so or not, to log in. In addition, in this option you can also see the devices that have done it in the past, in case you want to revoke access to a specific one
How to recover a hacked Instagram account
Safety, security and safety
As you can see, all the security measures are always few when it comes to protecting those accounts where we can have information or data of great value on a personal level. Instagram is a service that, although it is sometimes used in a banal way, on other occasions it is used to keep a history of photos and moments with great sentimental value. Not counting those who manage to make use of said network their way of generating income.
Therefore, it is important to know and take advantage of each security measure that is given. Because prevention is better than cure.